Act Upon letsbloom’s Insights
Reviewing Results
Overview
Technology innovation is rapidly transforming every industry. However, systems must comply with jurisdiction-specific regulations while operating in a regulated industry.
At letsbloom, we aim to help you grow your cloud-based business with bank-grade security and compliance. We have distilled common regulatory and benchmark frameworks to codify a set of control checks. Your infrastructure as code and container images are scanned and assessed against the control checks to present a health report. The health report furnishes insights into your application's security and compliance gaps. Filling the gaps will improve the cybersecurity posture of your app and help comply with cybersecurity regulations.
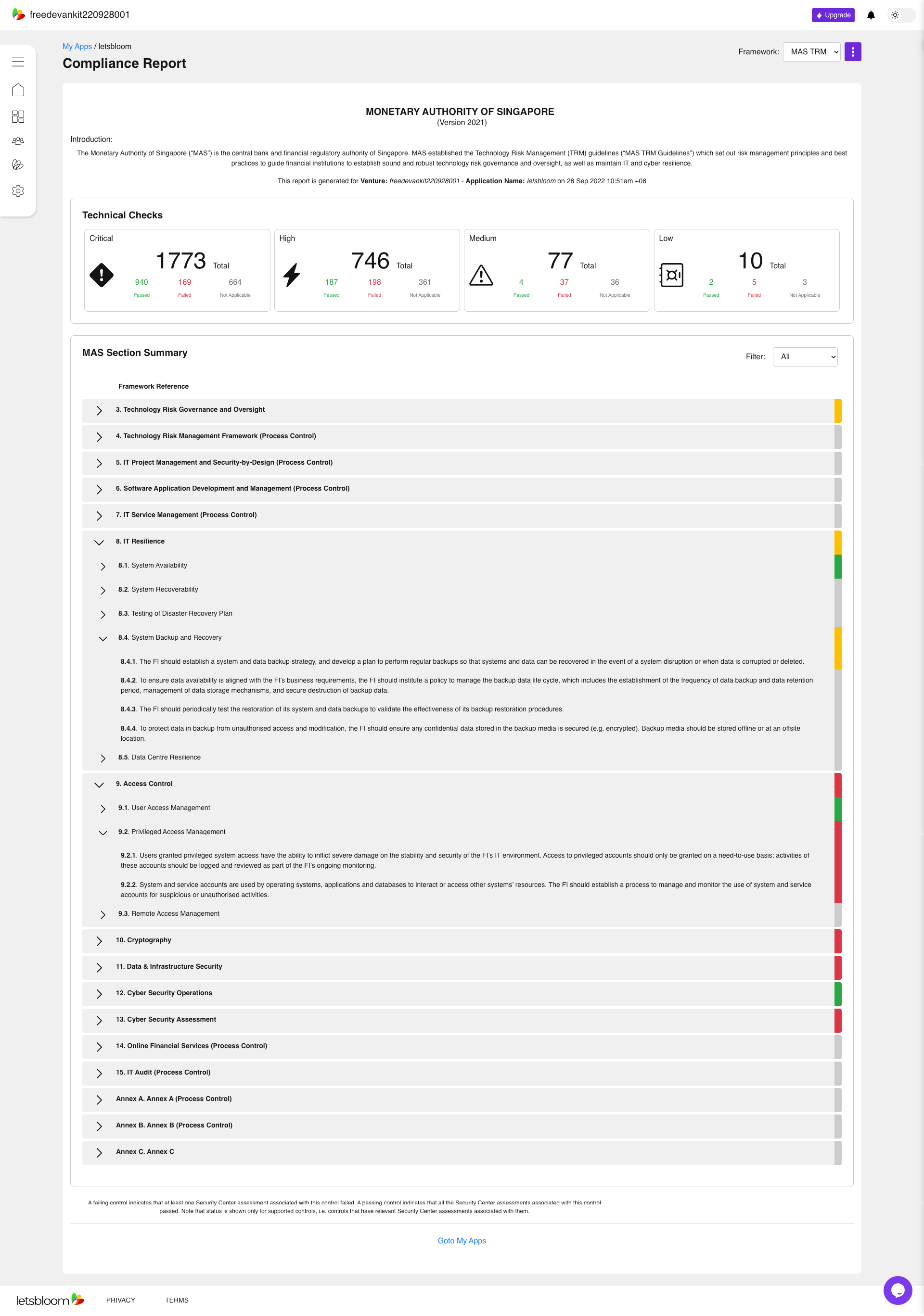
letsbloom platform presents the results through regulatory and benchmark lenses. This aspect enables you identify and prioritize issues using a threat-based approach specific to your application. Moreover, the results are aggregated into domains representing a set of controls with a regulatory or benchmark framework. While the framework simplifies compliance assessment, we, at letsbloom, believe that it’s imperative to have a threat-based view of your cybersecurity posture so that you can prioritize fixes based on their severity. Therefore, the findings with each domain are ranked based on the severity so you can fix the issues accordingly.
The regulatory and benchmark frameworks not only focus on technical control verification but also checks the effectiveness of the organizational processes and controls. Therefore, the platform features some domains which are marked exclusively for process controls. The controls in this domain validates the existence and effectiveness of the associated organizational processes. The platform also features domains that have a mix of technical controls and process controls.
letsbloom’s Starter tier automatically scans your infrastructure as code and container images and validates the technical controls. So, the health report highlights the status only for the domains that have technical controls. On the other hand, Premium and Enterprise tiers allows you to leverage letsbloom’s platform as a service to securely deploy and run your applications. You can use our platform and managed services to enforce process controls to enhance the cybersecurity posture and achieve compliance. For more details on our tiers and complete feature list, please refer to our Feature Comparison page.
The health assessment report highlights the status of your code in Red, Amber, Green, or Grey indications based on the number and criticality of the technical controls missing in your code.
Red : The red status indicates that your code missed one or more critical technical controls which might make your application prone to cybersecurity and non-compliance risks.
Amber : The amber status indicates that though your code has majority of technical controls, it is still missing a few controls which make your application prone to cybersecurity and non-compliance risks.
Green : The green status indicates that your code has all the critical and robust technical controls for that domain, but there might be some medium or low level controls that can improve the applications cybersecurity posture.
Grey : The grey status indicates that either the controls in that domain are not applicable for your application or you have not provided any infrastructure as code for scanning, or it’s a process control domain.
Individual Results
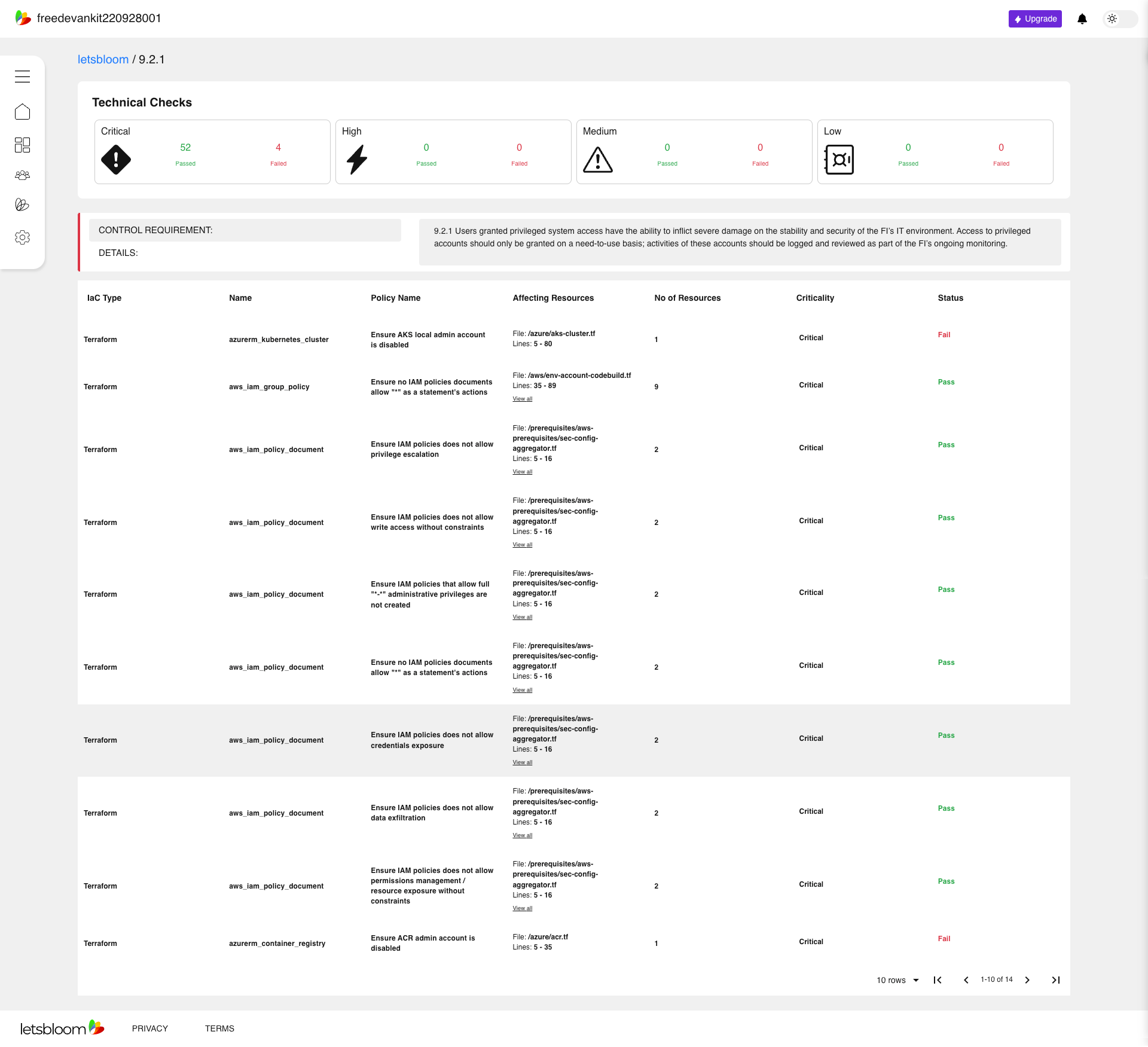
Coverage: The coverage percentage shown in the report represents the percentage of total number of controls within that domain that can be assessed during the scan.
There are two main reasons for the coverage to be less than 100%:
- Presence of control objectives which can be enforced through organizational processes only i.e., process controls.
- Starter tier performs pre-deployment scans only i.e., it can statically assess your infrastructure as code and container images. There are technical controls that are only enforceable during or post deployment. You can assess these controls using our ‘Premium’ or ‘Enterprise’ tier.
In this example, as a Starter account is used, the application is assessed against 69% of the regulatory requirements related to data and infrastructure security. After upgrading to premium level, the application will be assessed against 96% of the regulatory requirements.
Severity: The health report displays the top 10 findings (ranked by the severity level) for each domain.
The severity levels can be assessed as the following:
- Critical : These issues are considered imperative as per the regulatory requirements, benchmarks, and industry standards. Moreover, the exploitation of these issues could easily lead to compromise or privilege escalation in the environment. Some examples include reducing external facing (internet) footprint, missing encryption, or overly permissive roles.
- High : These issues also represent significant risk and could lead to non-compliance. However, you need to perform a cost-benefit analysis of implementing these controls and perform a risk-based assessment and implementation.
- Medium : These controls can further improve your applications’ cybersecurity, performance, and resiliency posture.
- Low : These issues are related to development and security hygiene in the environment. Implementing these controls reduces the management overhead and improves the system security and stability.
Experience the most advanced Compliance Automation Platform today!

