What are the Best Practices for Security Compliance Management?

Ritika Jain
Nov 13, 2024


Today, more than ever, maintaining security compliance has become essential for businesses of all sizes and industries. With data breaches and cyberattacks increasing in sophistication and frequency, it is high time for organizations to implement strong security measures in order to safeguard their critical assets and operations.
This blog underscores the importance of security compliance management and the best practices to help businesses to stay secure and resilient in today’s dynamic threat landscape.
What is Security Compliance Management?
Security compliance management involves implementing and maintaining strong security policies, procedures, and controls that help improve overall security posture, while complying with relevant laws, regulations, and industry standards such as GDPR, ISO 27001, NIST CSF, SOC 2, PCI DSS, FedRAMP, and CCPA.
This includes understanding the regulatory requirements relevant to your business, establishing policies and procedures to meet those requirements, and implementing necessary security controls to protect sensitive data and systems.
Why is Security Compliance Management Important?
Below are some of the key benefits of establishing strong security compliance management framework:
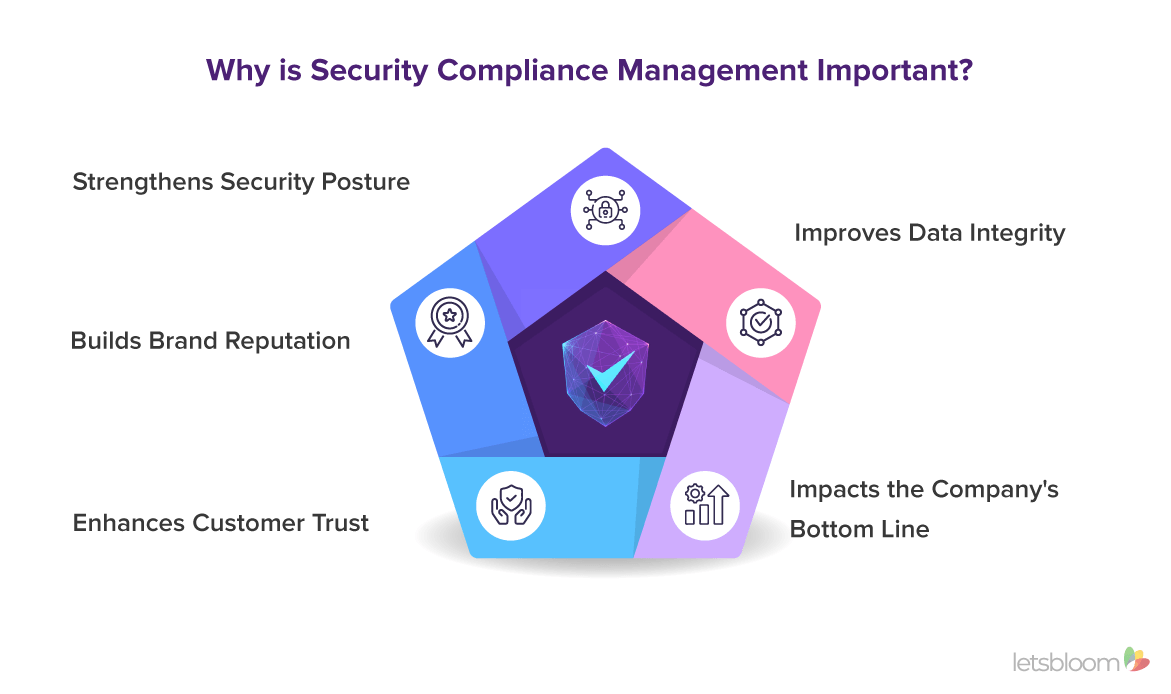
- Strengthens Security Posture: Security compliance efforts contribute to a stronger overall security framework. By implementing necessary security controls and practices, organizations strengthen their defenses against cyber threats, reducing the risk of data breaches and unauthorized access.
- Improves Data Integrity: By ensuring security compliance, organizations can maintain data integrity, reliability, availability and consistency, which is vital for informed decision-making and operational efficiency.
- Impacts the Company's Bottom Line: Security compliance helps organizations avoid hefty fines and penalties for non-compliance. Additionally, effective security compliance management can lead to reduced operational costs, improved efficiency, and better resource allocation.
- Enhances Customer Trust: Security compliance demonstrates to customers that your organization is handling their data securely and in line with regulatory requirements. This builds confidence and trust, which are essential for maintaining long-term relationships.
- Builds Brand Reputation: A strong security compliance builds your organization's reputation, positioning it as a responsible and trustworthy entity. This can attract new customers, investors, and business partners, while also boosting brand value and market competitiveness.
Best Practices for Effective Security Compliance Management
Adopt the following best practices to keep your organization secure and compliant:
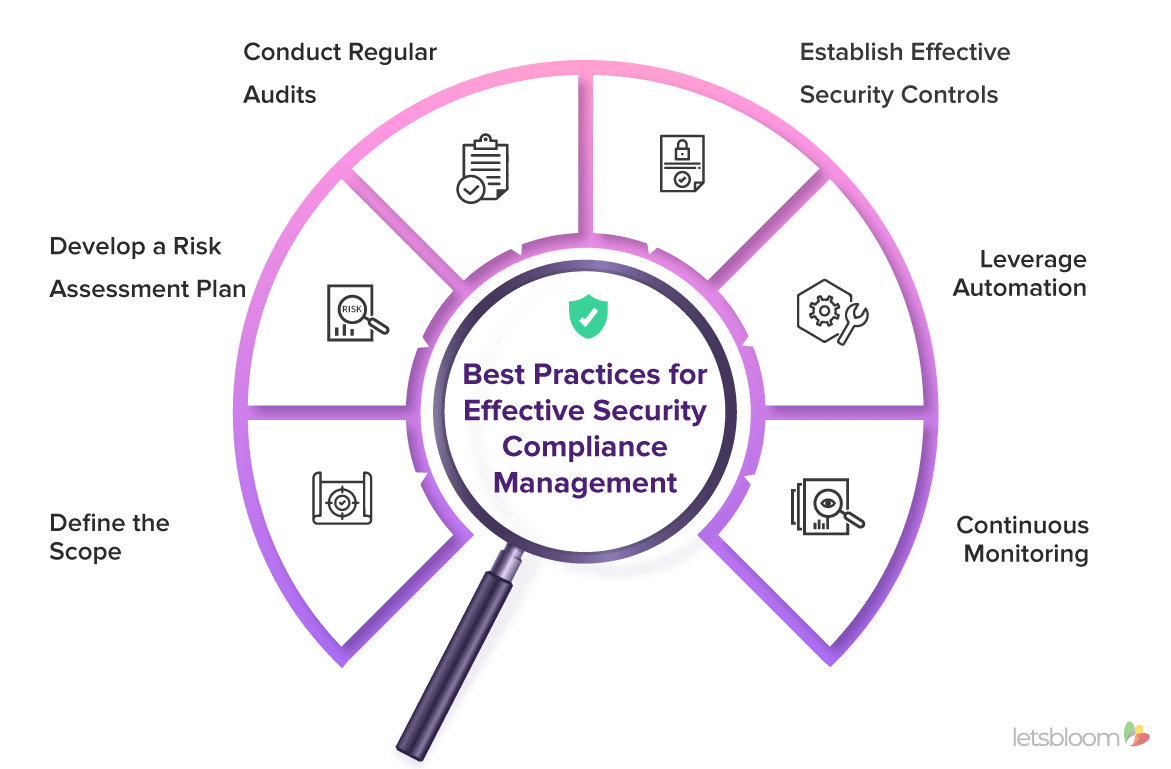
- Define the Scope: Identify the security standards and regulations applicable to your organization based on your industry, geographic presence, and the nature of data handled. Once the specific requirements are gathered, map out the scope of your security compliance program, including the systems, processes, and data.
- Develop a Risk Assessment Plan: Conducting a thorough security risk assessment helps identify and prioritize risks and gaps in your security posture. Evaluate the potential impact and likelihood of each risk and develop suitable remediation strategies. Regularly review and update the risk assessment to stay on par with the changing threats and vulnerabilities.
- Conduct Regular Audits: Security compliance audits are essential for maintaining strong security posture. Regularly assess your organization’s policies, procedures, and controls against the established standards and address the gaps before they escalate into major issues.
- Establish Effective Security Controls: Implement robust security controls to address the risks identified in the risk assessment. Regularly review and update these controls to ensure their effectiveness and alignment with changing threats and technologies.
- Leverage Automation: Automation tools can effectively streamline security compliance processes, reducing manual efforts and minimizing human errors.
- Continuous Monitoring: Security compliance is not a one-time activity but an ongoing effort. Continuous monitoring is imperative to maintain security compliance in today’s dynamic cybersecurity landscape. Leverage monitoring tools to gain complete visibility into your security compliance posture in real-time, enabling you to swiftly identify and address any potential risks.
Also Read: SOC 2 Compliance Check – A Detailed Guide
Conclusion
Effective security compliance management is crucial for protecting critical assets and maintaining operational integrity. By adopting best practices, organizations can enhance their security posture, build customer trust, and protect their brand reputation.
Ready to take your security compliance to the next level? Partner with letsbloom today and stay ahead of the curve in managing security and compliance in the cloud. Contact us!










