SOC 2 Compliance Checklist: The Ultimate Guide to Prepare for SOC 2 Audit

Ritika Jain
Sep 30, 2024


Table of contents
Data security and privacy are need of the hour in today’s world. With the global average cost of a data breach reaching USD 4.88 Million in 2024 - the highest total ever, businesses must safeguard their data, people, infrastructure, and their organization’s bottom line. Implementing data security frameworks and standards like SOC 2 (System and Organization Controls) can help strengthen your data security programs, protecting critical assets and data spread across multiple environments.
This guide offers a comprehensive checklist to help you fast-forward your journey to SOC 2 compliance and build the trust with your customers and stakeholders.
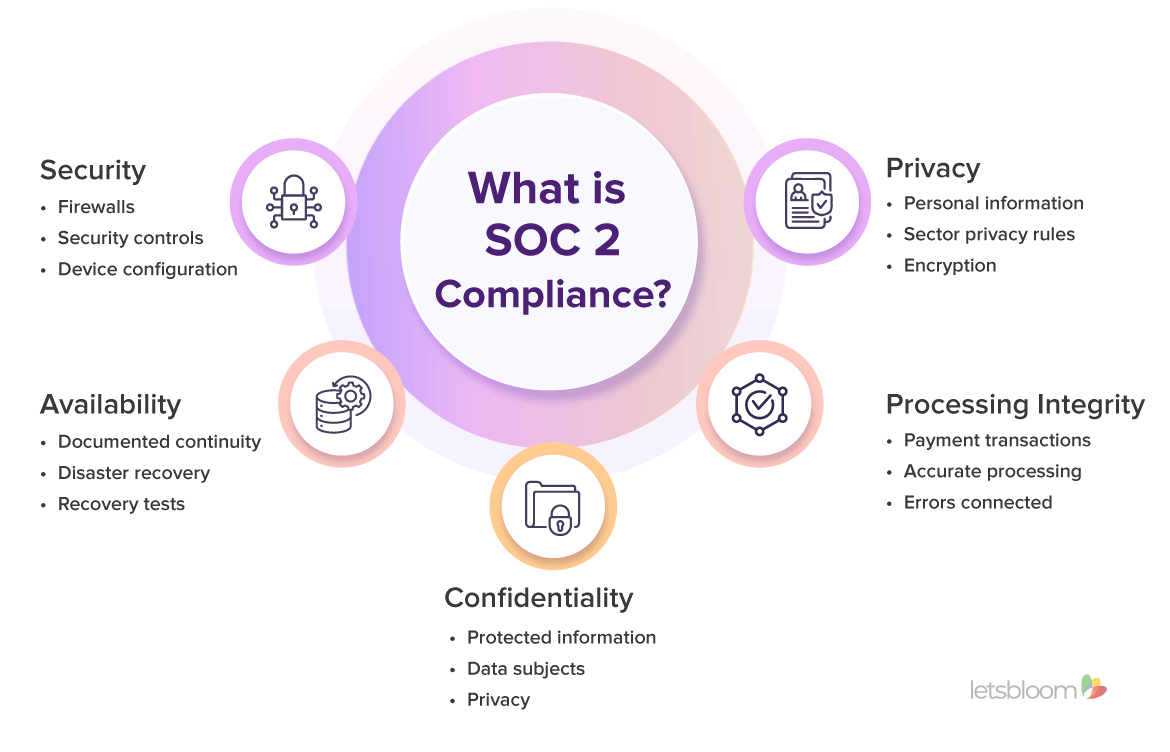
What is SOC 2?
SOC 2 is a security compliance standard designed for service providers that handle customer data. It evaluates the effectiveness of the organization’s security controls, processes, and policies to ensure that they meet industry standards and best practices. SOC 2 compliance demonstrates how well a company has implemented adequate security controls with regards to the five Trust Services Criteria (TSC): Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Types of SOC 2 Compliance Audits
There are two types of SOC 2 audit reports: Type 1 and Type 2.
A SOC 2 Type 1 report evaluates the design of security processes and controls at a specific point in time, while SOC 2 Type 2 report assesses the design as well as the operative effectiveness of these controls over a longer period of time, typically 6 months to a year.
The type of report an organization pursues depends on their specific needs and requirements. Type 1 is often a preliminary step, with Type 2 providing more comprehensive and ongoing assurance.
Difference between SOC 2 Type 1 and Type 2
| SOC 2 Type 1 | SOC 2 Type 2 | |
|---|---|---|
 Time to Achieve* Time to Achieve* |
3-6 months | 6-12 months |
 Cost Cost |
Least expensive | Most expensive |
 What it Does What it Does |
Short-term solution to demonstrate compliance - snapshot of security controls at single point in time | Long-term solution to demonstrate compliance - ongoing effectiveness of security controls over time, detailed descriptions on the auditor tests |
 Pros Pros |
Shorter audit windows, faster and less expensive | Provides a greater level of trust with clients and partners |
 Cons Cons |
May not provide enough assurance and may eventually need a Type II | Longer audit window, more expensive |
 Renewal Renewal |
Every 12 months | Every 12 months |
| *Dependent on size of the organization and the organization's readiness level | ||
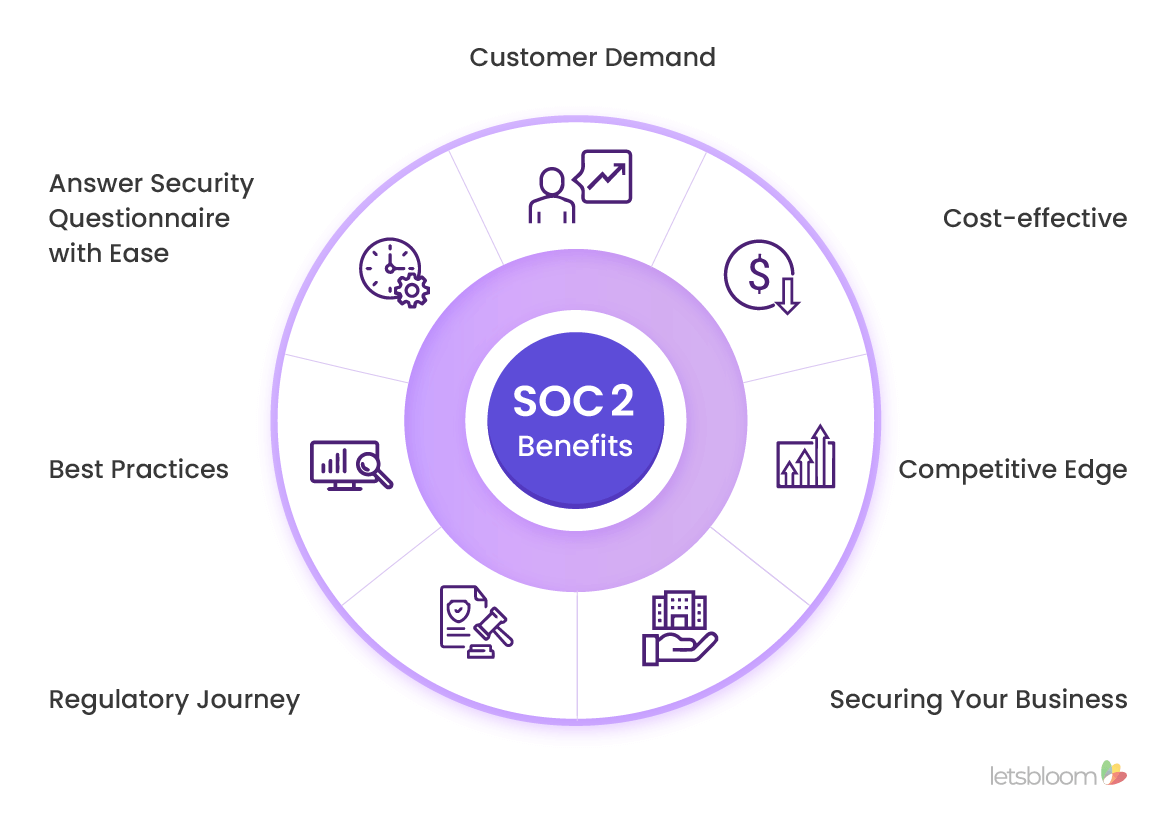
Why is SOC 2 Compliance Important for Your Business?
Achieving SOC 2 compliance offers several benefits that enhance an organization's reputation and market standing:
Building Customer Trust
SOC 2 certification demonstrates to customers that their data is secure and handled with integrity. This can be a significant competitive advantage, especially when dealing with sensitive information.
Competitive Advantage
With increasing data privacy regulations and security concerns, SOC 2 compliance sets your business apart. It shows prospective clients and partners that you take data security seriously, potentially winning you more business.
Expanding Market Opportunities
Many industries, particularly those heavily regulated, require SOC 2 compliance as a prerequisite for doing business. By achieving this certification, you open doors to new markets and opportunities.
What is a SOC 2 Compliance Checklist?
A SOC 2 compliance checklist is essential for any organization preparing for a SOC 2 audit. It outlines the necessary steps and requirements needed for achieving and demonstrating compliance with the TSC. This checklist enables businesses to simplify, streamline, and speed up their journey to SOC 2 compliance, saving time and resources. It also helps ensure that no crucial aspect of SOC 2 compliance is overlooked, providing a structured framework for achieving certification.
This guide offers a comprehensive checklist to help you fast-forward your journey to SOC 2 compliance and built the trust with your customers and stakeholders. Download the eBook now!
SOC 2 Compliance Checklist Ultimate Guide
Fast-forward your journey to SOC 2 compliance & build the trust with your customers and stakeholders.










