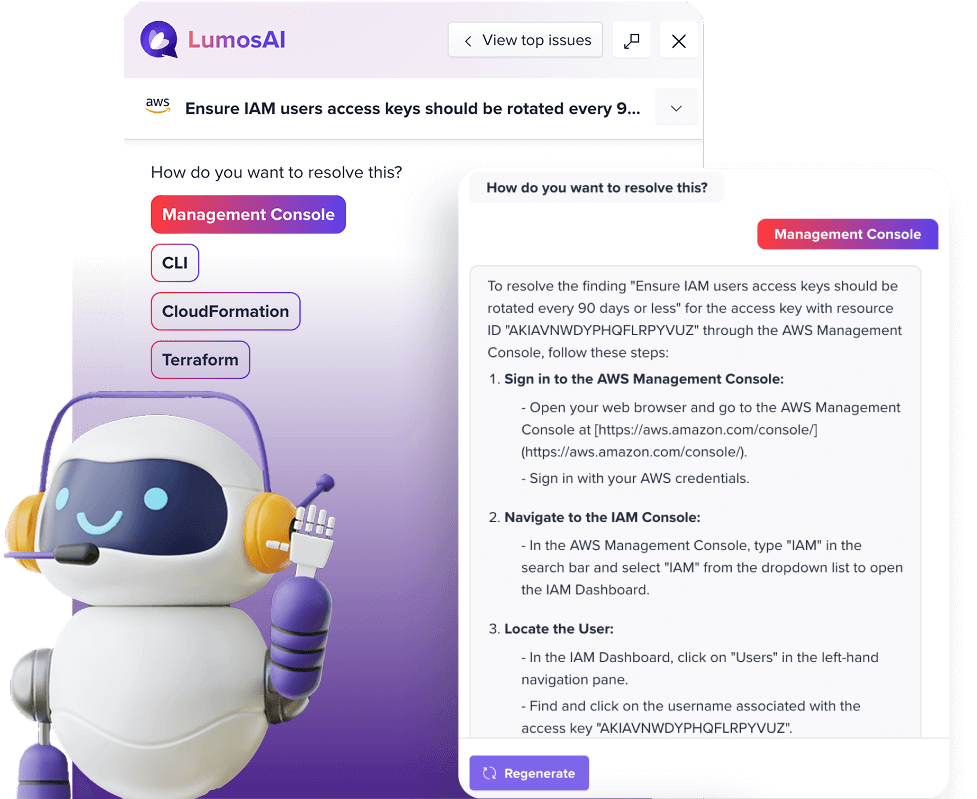
Latest Resources
Stay ahead with our insightful blogs, whitepapers, guides, and events that shed light on the latest trends and best practices of cloud & Gen AI security and compliance trends.
Latest Resources
Stay ahead with our insightful blogs, whitepapers, guides, and events that shed light on the latest trends and best practices of cloud & Gen AI security and compliance trends.

News
letsbloom Recognized in the 2025 Gartner® Market Guide for DevOps Continuous Compliance Automation Tools
letsbloom announced it has been recognized in the 2025 Gartner® Market Guide for DevOps Continuous Compliance Automation Tools. Connect with us to know how embedding compliance as code into the DevOps toolchain can boost lead time by 15%.
Know More
eBook
SOC 2 FAQs Playbook: A 101 Guide to SOC 2 Compliance
Let’s face it: you’re here because you need SOC 2. Whether you’re chasing bigger clients or prepping for due diligence, SOC 2 is your ticket to the big stage.
Know More
Blog
Tips to Navigate the 5 Key Security Shifts of 2025
Mega breaches are increasing in number, scale, and cost! By 2025, the global cost of cybercrime is projected to reach $10.5 trillion, growing at 15 percent annually. To counter rising risks in today’s complex threat environment, companies are investing in building a robust cybersecurity posture.
Know More
Blog
Finastra Data Breach: Key Lessons from the 400GB Data Exposure Attack
Finastra, a leading London-based financial software company, is investigating a data breach involving its internal file-transfer platform.
Know More
eBook
ISO 27001 Checklist – The Ultimate Guide to Prepare for ISO 27001 Audit
Let’s explore the key components of the ISO 27001 checklist and how you can use it to fortify your organization’s defenses.
Know More
Blog
What are the Best Practices for Security Compliance Management?
Today, more than ever, maintaining security compliance has become essential for businesses of all sizes and industries.
Know More
News
letsbloom Recognized in the 2025 Gartner® Market Guide for DevOps Continuous Compliance Automation Tools
letsbloom announced it has been recognized in the 2025 Gartner® Market Guide for DevOps Continuous Compliance Automation Tools. Connect with us to know how embedding compliance as code into the DevOps toolchain can boost lead time by 15%.
Know More
eBook
SOC 2 FAQs Playbook: A 101 Guide to SOC 2 Compliance
Let’s face it: you’re here because you need SOC 2. Whether you’re chasing bigger clients or prepping for due diligence, SOC 2 is your ticket to the big stage.
Know More
Blog
Tips to Navigate the 5 Key Security Shifts of 2025
Mega breaches are increasing in number, scale, and cost! By 2025, the global cost of cybercrime is projected to reach $10.5 trillion, growing at 15 percent annually. To counter rising risks in today’s complex threat environment, companies are investing in building a robust cybersecurity posture.
Know More
Blog
Finastra Data Breach: Key Lessons from the 400GB Data Exposure Attack
Finastra, a leading London-based financial software company, is investigating a data breach involving its internal file-transfer platform.
Know More
eBook
ISO 27001 Checklist – The Ultimate Guide to Prepare for ISO 27001 Audit
Let’s explore the key components of the ISO 27001 checklist and how you can use it to fortify your organization’s defenses.
Know More
Blog
What are the Best Practices for Security Compliance Management?
Today, more than ever, maintaining security compliance has become essential for businesses of all sizes and industries.
Know More